Ledger Authentication Module (LAM)
warning
Using Ledger Authentication Module to authenticate via API will be supported until Q3 2024, if you are starting a new setup, we recommend using the new API User methods
To register API operators able to perform or approve transactions programmatically, you will need to set up the Ledger Authentication Module (LAM).
The LAM is your internal secure gateway to the Ledger Enterprise API. It exposes a simple, easy-to-use, and secure REST API enabling you to interact with your Ledger Enterprise workspace.
Running the Ledger Authentication Module (LAM)
The LAM runs in your infrastructure as a standalone Docker container. The following diagram describes how the LAM communicates with your Ledger Enterprise workspace.
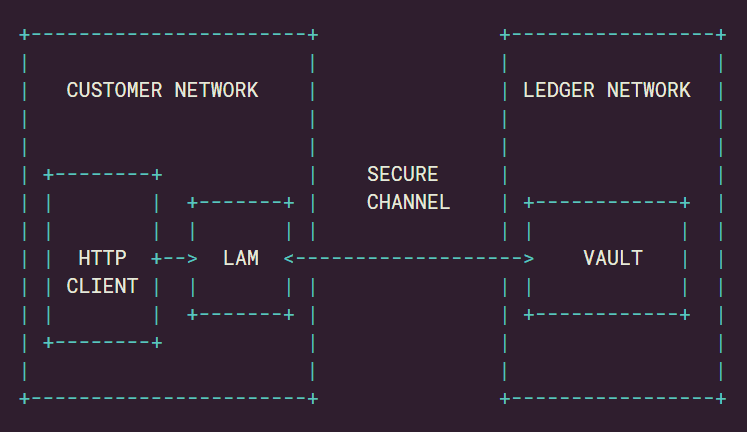
This design resembles the way operators’ Personal Security Devices connect to the Ledger Vault platform. You can think of the following analogy: Workspace UI + Personal Security Device <=> Http Client + LAM
Ledger Security
We use hardware secure elements to keep your secrets safe in the Ledger network when you are using LAM. However, some sensitive information lies in your own network.
Because it’s hard to ensure the same level of security on standard machines than it is on dedicated secure elements, special care must be taken to secure the machine running LAM.
The authentication between LAM and the Ledger Vault is a transparent process that is entirely handled by LAM.
Ledger will provide you a signed certificate following your Certificate Signing Request (CSR) that will be used to trust your messages to the Vault.
Hence, the only link needed to access the Vault is between this Docker running container. In demo mode Ledger will provide you everything already setup so you just need the API url and Authentication.
Data Flow Summary
The following diagram summarizes the interactions you could have with LAM. It highlights the data flows in the current state of LAM.
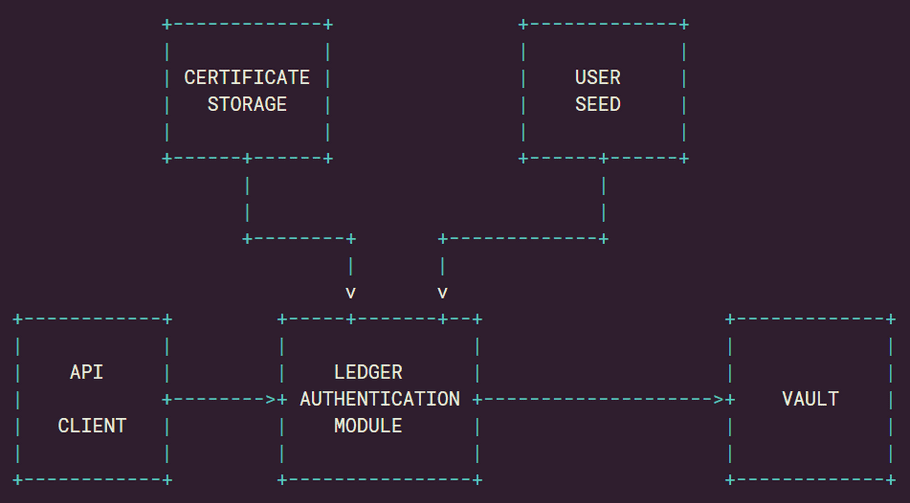
warning
Set up the User Seed and Certificate Storage volumes carefully as they contain sensitive information, especially in the production stage. If necessary, we can assist you during this process.
Security
The primary reason for accessing the Vault using a Ledger certified hardware (i.e. the Ledger Blue) is that we have been able to assess with reasonable certainty that your secret is secure in this framework.
The purpose of LAM is to act as a certified device, although it isn’t a Ledger validated Hardware device, nor does it run on hardware that is certified by Ledger.
The only channel on which we have full control is the communication between LAM and the Vault.
The sensitive information required by LAM to communicate with the Vault is held by you. It is accessible to LAM through shared volumes and is composed of your LAM certificate and your API users seeds.
📜 Certificate
The LAM certificate, issued by Ledger, is used to initialize the secure channel between LAM and the Vault HSM. If you use multiple environments, a unique certificate will be issued for each.
👤 API users’ seeds
The seeds are generated on demand by LAM. They’re made of 24 words, which means they are 256 bits BIP39 seed phrases. For more details on seed phrases, see the Bitcoin wiki.